What Is xmlrpc.php?
The xmlrpc.php file is a part of WordPress that enables remote connections to your website. It was originally designed to help external apps like mobile apps or publishing tools to interact with WordPress. But in 2024, most sites don’t use it. And even if you don’t use it, it’s still accessible by default, and frequently targeted by hackers.
How xmlrpc.php Gets Exploited
Hackers use xmlrpc.php for:
- Forceful Attacks: Sending thousands of login attempts in a single request.
- DDoS Attacks: Using your site to flood another target with traffic.
- Pingback Abuse: Turning your site into a tool for larger-scale exploits.
- Remote Code Execution: In rare cases, insecure configurations allow code injection.
Even if they don’t succeed, these requests can slow down your server and consume resources, affecting site performance.
Unless you're using specific tools that require it (like Jetpack or external publishing apps), the best thing to do is to completely block access to this file. And the easiest way to do that is with WordPress Manager by Softaculous.
Here’s how to block xmlrpc.php with WordPress manager:
STEP 1: Log in to your cPanel.
There are three methods to log into your cPanel.
- Method 1: Log in to your cPanel directly.
- Method 2: Log in to your cPanel through your Customer Portal.
Through your Customer Portal;
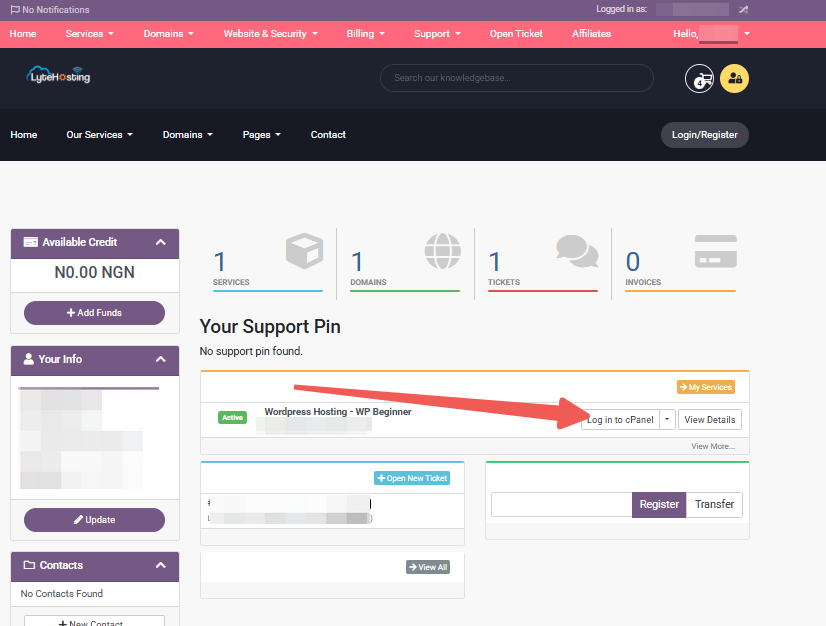
- Log in to your Customer Portal.
- Click on "Log in to cPanel".
- Method 3: Log in using the details sent to your Email.
Through your Email;
- When you purchase a hosting plan, your cPanel login details (including username, password, and cPanel URL) are automatically sent to your registered email address. Simply check your inbox (or spam folder), locate the email, and use the provided credentials to access your cPanel.
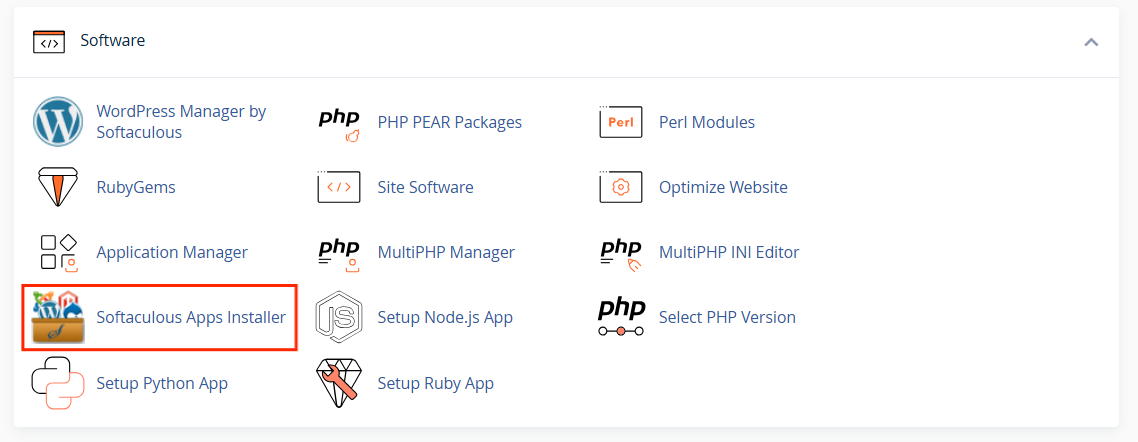
STEP 2: Locate the Software section and click on Softaculous Apps Installer.
STEP 3: Click the box for Installations.
An alternative is to select the “All Installations” icon from the menu in the upper-right corner.
![]()
STEP 4: Click the WordPress icon next to the installation you want to manage.
![]()
STEP 5: In WordPress Manager, select the website you want to secure.
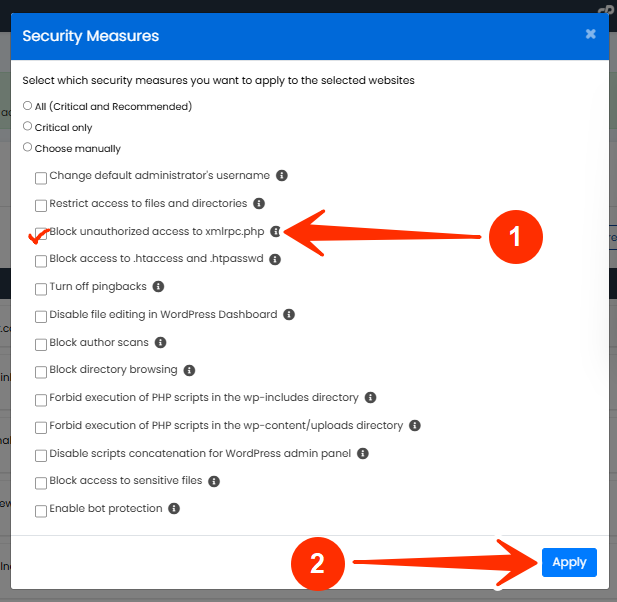
STEP 6: Scroll to the Security Measures section.
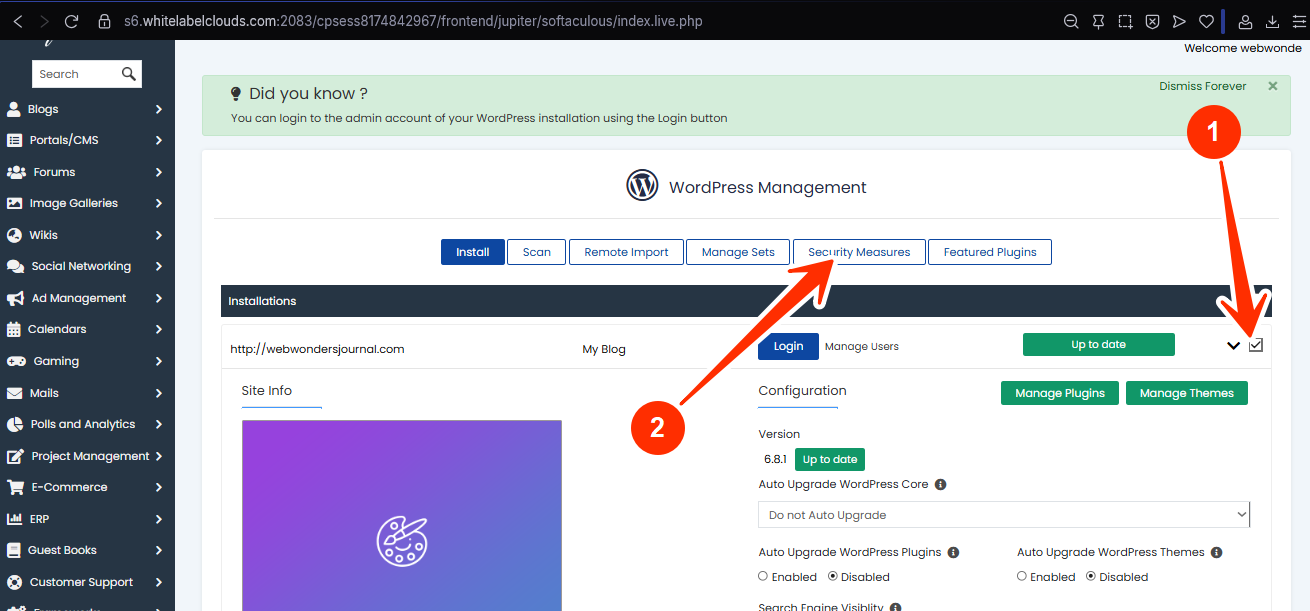
STEP 7: Checkmark the box for “Block unauthorized access to xmlrpc.php”, and click Apply.
NOTE: If you’ve manually edited your .htaccess file or use custom security rules, those directives might override this setting. In most cases, though, WordPress Manager’s block will take priority.
How to Know If you’re Being Targeted through xmlrpc.php
Look for:
- Sudden spikes in server usage.
- Login attempts even when you’ve disabled login forms.
- Security plugin logs showing repeated access to xmlrpc.php.
- Error logs mentioning failed XML-RPC requests.
If you see any of the above, block xmlrpc.php immediately.
Frequently Asked Questions (FAQs)
Q: Will disabling xmlrpc.php break anything on my site?
Not unless you’re using tools like Jetpack, the WordPress mobile app, or some remote publishing software. If you’re unsure, disable it and test your features.
Q: Can I re-enable it later?
Yes, with WordPress Manager, you can undo the block in one click.
Q: Is disabling xmlrpc.php better than rate-limiting it?
Yes. Full blocking is safer unless you need it. Rate-limiting only slows the attack down, but doesn’t eliminate the risk.
If you need help, kindly contact LyteHosting support.




